Abstract
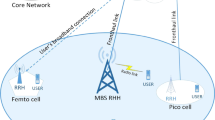
Massive machine type communication (mMTC) is a key use case that is expected to be supported by 5G NR. One of the key challenges in 5G NR communications for mMTC use case is to enhance the initial access procedure to overcome the problem of congestion and overloading from mMTC devices. The intermittent blockages in the mmWave frequency range of 5G further degrade the random access performance significantly. 5G NR introduces the concept of numerology where multiple types of sub-carrier spacing is allowed. To circumvent the problem of random access performance enhancement, we propose a blockage aware adaptive numerology to maximize the number of devices that can be connected to the cellular network. In this paper, the problem of selecting optimal numerology for random access is modelled as a contextual multi-arm bandit framework while taking the blockages and their mobility pattern in the cell at a given time into account. We consider the upper confidence bound (UCB) action selection method to take the uncertainty of rewards of numerologies at a given instance into account. The proposed adaptive numerology solution maximizes the number of devices joining the network per RACH occasion and also minimizes the average joining time of a device when compared to fixed numerology schemes.











Similar content being viewed by others
Availability of data and materials
Data sharing not applicable to this article as no datasets were generated or analysed during the current study.
Notes
Data sharing not applicable to this article as no datasets were generated or analysed during the current study.
References
Ericson mobility report. (November, 2021)
Ahrend U, Aleksy M, Berning M, Gebhardt J, Mendoza F, Schulz D (2021) Sensors as the basis for digitalization: New approaches in instrumentation, iot-concepts, and 5g. Internet of Things 15:100406
3GPP: Technical Specifications Group RAN: About Release 16. Technical specification (ts) (April 2020). http://www.3gpp.org/release-16
3GPP Technical Specifications Group RAN (2020) NR Physical Channels and Modulations (Release 15). Technical Specification (TS) 38.211 (January 2020). Version 15.8.0
Series M (2015) Imt vision-framework and overall objectives of the future development of imt for 2020 and beyond. Recommendation ITU 2083:21
3GPP Technical Specifications Group RAN (2020) Medium Access Control (MAC) Protocol Specification (Release 15). Technical Specification (TS) 38.321 (January 2020). Version 15.8.0
Raftopoulou M, Jorguseski L, Litjens R (2019) Design and assessment of low-latency random access procedures in 5g networks. In: 2019 European Conference on Networks and Communications (EuCNC), pp. 406–411 2019
Das SS, De Carvalho E, Prasad R (2008) Performance analysis of ofdm systems with adaptive sub carrier bandwidth. IEEE. Trans. Wirel. Commun 7(4):1117–1122
Arslan H et al (2018) Flexible multi-numerology systems for 5g new radio. J. Mob, Multimed
Firyaguna F, Kibilda J, Marchetti N (2019) Application of flexible numerology to blockage mitigation in 5g-mmwave networks. In: 2019 IEEE Global Communications Conference (GLOBECOM), pp. 1–6. IEEE
Korrai PK, Lagunas E, Bandi A, Sharma SK, Chatzinotas S (2020) Joint power and resource block allocation for mixed-numerology-based 5g downlink under imperfect csi. IEEE Open Journal of the Communications Society 1:1583–1601. https://doi.org/10.1109/OJCOMS.2020.3029553
Yang W, Qin Y, Yang Z (2020) A reinforcement learning based data storage and traffic management in information-centric data center networks. Mobile Networks and Applications 1–10
Zhang J, Xu X, Zhang K, Zhang B, Tao X, Zhang P (2019) Machine learning based flexible transmission time interval scheduling for embb and urllc coexistence scenario. IEEE Access 7:65811–65820
Flores de Valgas J, Monserrat JF, Arslan H (2021) Flexible numerology in 5g nr: Interference quantification and proper selection depending on the scenario. Mob Inf Syst 2021
Thota J, Aijaz A (2019) On performance evaluation of random access enhancements for 5g urllc. In: 2019 IEEE Wireless Communications and Networking Conference (WCNC), pp. 1–7. IEEE
Marijanovic L, Schwarz S, Rupp M (2018) Optimal numerology in ofdm systems based on imperfect channel knowledge. In: 2018 IEEE 87th Vehicular Technology Conference (VTC Spring), pp. 1–5. IEEE
You L, Liao Q, Pappas N, Yuan D (2018) Resource optimization with flexible numerology and frame structure for heterogeneous services. IEEE Commun Lett 22(12):2579–2582. https://doi.org/10.1109/LCOMM.2018.2865314
Tang C, Chen X, Chen Y, Li Z (2019) dynamic resource optimization based on flexible numerology and markov decision process for heterogeneous services. In: 2019 IEEE 25th International Conference on Parallel and Distributed Systems (ICPADS), pp. 610–617. IEEE
Jain IK, Kumar R, Panwar S (2018) Limited by capacity or blockage? a millimeter wave blockage analysis. arXiv:1808.01228
Bai T, Vaze R, Heath RW (2014) Analysis of blockage effects on urban cellular networks. IEEE Transactions on Wireless Communications 13(9):5070–5083
Tse D, Viswanath P (2005) Fundamentals of wireless communication. Cambridge University Press
Das SS, De Carvalho E, Prasad R (2007) Variable sub-carrier bandwidths in ofdm systems. In: 2007 IEEE 65th Vehicular Technology Conference - VTC2007-Spring, pp. 1866–1870. https://doi.org/10.1109/VETECS.2007.387
Sutton RS, Barto AG (2018) Reinforcement learning: An introduction. MIT press
Li L, Chu W, Langford J, Schapire RE (2010) A contextual-bandit approach to personalized news article recommendation. In: Proceedings of the 19th International Conference on World Wide Web, pp. 661–670
Rappaport TS, et al (1996) Wireless communications: principles and practice. prentice hall PTR New Jersey
Bommisetty L, Pawar S, Venkatesh T (2022) Performance analysis of random access mechanism in 5g millimeter wave networks: Effect of blockage, shadowing and mobility. IEEE Access 10:69091–69105
Walsh TJ, Szita I, Diuk C, Littman ML (2012) Exploring compact reinforcement-learning representations with linear regression. arXiv:1205.2606
Funding
No funding was received to assist with the preparation of this manuscript.
Author information
Authors and Affiliations
Contributions
All authors contributed to the study conception and design. Material preparation, data collection and analysis were performed by Lokesh Bommisetty. The first draft of the manuscript was written by Lokesh Bommisetty and it was proofread, rewritten by TG Venkatesh. The work was supervised by TG Venkatesh.
Corresponding author
Ethics declarations
Competing Interests
The authors have no competing interests to declare that are relevant to the content of this article.
Consent for publication
Authors declare their consent for publication as per Springer publication guidelines.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix A Convergence Bound for Linear UCB
Appendix A Convergence Bound for Linear UCB
Considering the linear estimate of the coefficients as given in Eq. 16, the convergence of the reward can be explained as follows. With at least a probability of \(1-\delta \), the convergence bound given in (A1) holds good for any \(\delta > 0\) and \(\varvec{x}_{t,a} \in \mathbb {R}^d\),
where \(\gamma =1+\sqrt{ln(2/\delta )/2}\) is a constant. In other words,
The parameter \(\gamma \) controls the degree of exploration of numerologies with low experience. In other words, as \(\gamma \) increases, the exploration of new arms of less experienced arms is more encouraged. The above convergence has been proven in [27] for the first time and then applied to contextual bandits in [24].
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Bommisetty, L., Venkatesh, T. Contextual Bandit Based Adaptive Numerology for Initial Access in 5G NR Networks. Mobile Netw Appl (2023). https://doi.org/10.1007/s11036-023-02199-3
Accepted:
Published:
DOI: https://doi.org/10.1007/s11036-023-02199-3