Abstract
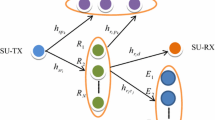
We study the physical-layer security of multi-hop secondary network under spectrum sharing constraint caused by the primary, which consists of many simultaneously independent direct transceiver pairs. The existence of a secondary eavesdropper, which attempts to hear confidential information, results in secure communication to be needful. The PUs’ interference forces low secondary SIRs. The secondary power constraint according to PUs causes the QoS to diminish, especially when the PUs transmission simultaneously operates. In this paper, we derive the closed-form of end-to-end multi-hop secrecy outage probability expression with independent non-identically distributed (i.n.i.d) Rayleigh fading. Furthermore, the secondary intercept probability is derived. Combining the outage probability, we present the security-reliability of the system. Besides, the impact of different numbers of primary transceivers on end-to-end multi-hop outage probability is investigated. Finally, our theoretical results verified via extensive Monte Carlo simulations.







Similar content being viewed by others
References
Yang, L., Chen, J., Kuo, Y., & Zhang, H. (2014). Outage performance of DF-based cooperative multicast in spectrum-sharing cognitive relay networks. IEEE Communications Letters, 18(7), 1250–1253. https://doi.org/10.1109/LCOMM.2014.2327631.
Goldsmith, A., Jafar, S. A., Maric, I., & Srinivasa, S. (2009). Breaking spectrum gridlock with cognitive radios: An information theoretic perspective. Proceedins of the IEEE, 97(5), 894–914. https://doi.org/10.1109/JPROC.2009.2015717.
Gu, Y., & Aïssa, S. (2014). Interference aided energy harvesting in decode-and-forward relaying systems. In 2014 IEEE international conference on communications (ICC), Sydney, NSW, Australia, 10–14 June 2014 2014 (pp. 5378–5382). IEEE. https://doi.org/10.1109/ICC.2014.6884176.
Duong, T. Q., Yeoh, P. L., Bao, V. N. Q., Elkashlan, M., & Yang, N. (2012). Cognitive relay networks with multiple primary transceivers under spectrum-sharing. IEEE Signal Processing Letters, 19(11), 741–744. https://doi.org/10.1109/LSP.2012.2217327.
Ngoc, P. T. D., Duy, T. T., Bao, V. N. Q., & Ho-Van, K. (2015). Performance enhancement for underlay cognitive radio with partial relay selection methods under impact of hardware impairment. In 2015 international conference on advanced technologies for communications (ATC), 14–16 Oct. 2015 2015 (pp. 645–650). https://doi.org/10.1109/ATC.2015.7388411.
Duy, T. T., Bao, V. N. Q., & Duong, T. Q. (2014). Secured communication in cognitive MIMO schemes under hardware impairments. In 2014 international conference on advanced technologies for communications (ATC 2014), 15–17 Oct. 2014 (pp. 109–112). https://doi.org/10.1109/ATC.2014.7043366.
Conne, C., & Kim, I.-M. (2010). Outage probability of multi-hop amplify-and-forward relay systems. IEEE Transactions on Wireless Communications, 9(2), 1139–1149. https://doi.org/10.1109/TWC.2010.03.090609.
Asghari, V., Costa, D Bd, & Aissa, S. (2012). Performance analysis for multihop relaying channels with Nakagami-m fading: Ergodic capacity upper-bounds and outage probability. IEEE Transactions on Communications, 60(10), 2761–2767. https://doi.org/10.1109/TCOMM.2012.081012.100156.
Duy, T. T., Anpalagan, A., & Kong, H. (2012). Multi-hop cooperative transmission using fountain codes over Rayleigh fading channels. Journal of Communications and Networks, 14(3), 267–272. https://doi.org/10.1109/JCN.2012.6253087.
Thanh, T. L., Bao, V. N. Q., & Duy, T. T. (2014). Capacity analysis of multi-hop decode-and-forward over Rician fading channels. In 2014 international conference on computing, management and telecommunications (ComManTel), Danang, Vietnam, 27–29 April 2014 (pp. 134-139). https://doi.org/10.1109/ComManTel.2014.6825593.
Nam, P. M., Duy, T. T., & Ca, P. V. (2019). End-to-end security-reliability analysis of multi-hop cognitive relaying protocol with TAS/SC-based primary communication, total interference constraint and asymmetric fading channels. International Journal of Communication Systems, 32(2), 1–16. https://doi.org/10.1002/dac.3854.
Rasethuntsa T. R., Kumar S., Kaur M. (2019). A comprehensive performance evaluation of a DF-based multi-hop system over \(\alpha -\kappa -\mu \) and \(\alpha -\kappa -\mu \)-extreme fading channels. arXiv:1903.09353.
Kumar, S., Chauhan, P. S., Raghuwanshi, P., & Kaur, M. (2018). ED performance over \(\alpha -\eta -\mu \)/IG and \(\alpha -\kappa -\mu \)/IG generalized fading channels with diversity reception and cooperative sensing: A unified approach. AEU - International Journal of Electronics and Communications, 97, 273–279. https://doi.org/10.1016/j.aeue.2018.10.027.
Tin, P. T., Nam, P. M., Duy, T. T., & Voznak, M. (2017). Security-reliability analysis for a cognitive multi-hop protocol in cluster networks with hardware imperfections. IEIE Transactions on Smart Processing & Computing, 6(3), 200–209. https://doi.org/10.5573/IEIESPC.
Duy, T. T., & Bao, V. N. Q. (2013) Multi-hop transmission with diversity combining techniques under interference constraint. In 2013 international conference on advanced technologies for communications (ATC 2013), 16–18 Oct. 2013 (pp. 131–135). https://doi.org/10.1109/ATC.2013.6698092.
Tran, D. T., & Bao, V. N. Q. (2013). Outage performance of cooperative multihop transmission in cognitive underlay networks. In 2013 international conference on computing, management and telecommunications (ComManTel), 21–24 Jan. 2013 (pp. 123–127). https://doi.org/10.1109/ComManTel.2013.6482377.
Nguyen, S. Q., & Kong, H. Y. (2016). Exact outage analysis of the effect of co-channel interference on secured multi-hop relaying networks. International Journal of Electronics, 103(11), 1822–1838. https://doi.org/10.1080/00207217.2016.1138534.
Duy, T. T., Trang, C. N., Bao, V. N. Q., & Hanh, T. (2015). Joint impact of hardware impairment and co-channel interference on multi-hop relaying. In 2015 international conference on advanced technologies for communications (ATC), 14–16 Oct. 2015 (pp. 88–92). https://doi.org/10.1109/ATC.2015.7388424.
Hieu, T. D., Duy, T. T., & Kim, B. (2018). Performance enhancement for multihop harvest-to-transmit WSNs with path-selection methods in presence of eavesdroppers and hardware noises. IEEE Sensors Journal, 18(12), 5173–5186. https://doi.org/10.1109/JSEN.2018.2829145.
Lee, J.-H. (2016). Optimal power allocation for physical layer security in multi-hop DF relay networks. IEEE Transactions on Wireless Communications, 15(1), 28–38. https://doi.org/10.1109/TWC.2015.2466091.
Lee, K., Chae, C., Heath, R. W., & Kang, J. (2011). MIMO transceiver designs for spatial sensing in cognitive radio networks. IEEE Transactions on Wireless Communications, 10(11), 3570–3576. https://doi.org/10.1109/TWC.2011.092711.101305.
Sulyman, A. I., Takahara, G., Hassanein, H. S., & Kousa, M. (2009). Multi-hop capacity of MIMO-multiplexing relaying systems. IEEE Transactions on Wireless Communications, 8(6), 3095–3103. https://doi.org/10.1109/TWC.2009.080655.
Hussein, J. A., Ikki, S. S., Boussakta, S., Tsimenidis, C. C., & Chambers, J. (2016). Performance analysis of a multi-hop UCRN with co-channel interference. IEEE Transactions on Communications, 64(10), 4346–4364. https://doi.org/10.1109/TCOMM.2016.2591522.
Nam, P. M., Ca, P. V., Tuan, P. V., Duy, T. T., & Bao, V. N. Q. (2018). Security versus Reliability Study for Multi-hop Cognitive M2M Networks With Joint Impact of Interference Constraint and Hardware Noises. Paper presented at the International Conference on Advanced Technologies for Communications, Ho Chi Minh. https://doi.org/10.1109/ATC.2018.8587460.
Fang, H., Xu, L., & Wang, X. (2018). Coordinated multiple-relays based physical-layer security improvement: A single-leader multiple-followers stackelberg game scheme. IEEE Transactions on Information Forensics and Security, 13(1), 197–209. https://doi.org/10.1109/TIFS.2017.2746001.
Do, N. T., & An, B. (2015). Secure transmission using decode-and-forward protocol for underlay cognitive radio networks. Paper presented at the 2015 seventh international conference on ubiquitous and future networks, Sapporo.
Shim, K., Do, N. T., & An, B. (2017). Performance analysis of physical layer security of opportunistic scheduling in multiuser multirelay cooperative networks. Sensors (Basel, Switzerland), 17(2), 377. https://doi.org/10.3390/s17020377.
Son, P. N., & Kong, H. Y. (2015). Cooperative communication with energy-harvesting relays under physical layer security. IET Communications, 9(17), 2131–2139. https://doi.org/10.1049/iet-com.2015.0186.
Ding, X., Song, T., Zou, Y., & Chen, X. (2016) Intercept probability analysis of relay selection for wireless communications in the presence of multiple eavesdroppers. In 2016 IEEE wireless communications and networking conference, 3–6 April 2016 (pp. 1–6). https://doi.org/10.1109/WCNC.2016.7564932.
Sun, G., Han, Z., Jiao, J., Wang, Z., & Wang, D. (2017). Physical layer security in MIMO wiretap channels with antenna correlation. China Communications, 14(8), 149–156. https://doi.org/10.1109/CC.2017.8014375.
Duy, T. T., & Son, P. N. (2015). Secrecy performances of multicast underlay cognitive protocols with partial relay selection and without Eavesdropper’s information. KSII Transactions on Internet and Information Systems, 9(11), 4623–4643. https://doi.org/10.3837/tiis.2015.11.021.
Kolokotronis, N., & Athanasakos, M. (2016) Improving physical layer security in DF relay networks via two-stage cooperative jamming. In 2016 24th European signal processing conference (EUSIPCO), Aug. 29 2016—Sept. 2 2016 (pp. 1173–1177). https://doi.org/10.1109/EUSIPCO.2016.7760433.
He, H., Ren, P., Du, Q., Sun, L., & Wang, Y. Jamming or Forwarding? Full-duplex relaying for physical layer security. In 2016 IEEE Globecom Workshops (GC Wkshps), 4–8 Dec. 2016 (pp. 1–6). https://doi.org/10.1109/GLOCOMW.2016.7848937.
Zheng, G., Choo, L. C., & Wong, K. K. (2011). Optimal Cooperative Jamming to Enhance Physical Layer Security Using Relays. IEEE Transactions on Signal Processing, 59(3), 1317–1322. https://doi.org/10.1109/TSP.2010.2092774.
Ding, X., Song, T., Zou, Y., & Chen, X. (2016). Security-reliability tradeoff for friendly jammer assisted user-pair selection in the face of multiple Eavesdroppers. IEEE Access, 4, 8386–8393. https://doi.org/10.1109/ACCESS.2016.2607783.
Cai, C., Cai, Y., Yang, W., & Yang, W. (2013). Secure connectivity using randomize-and-forward strategy in cooperative wireless networks. IEEE Communications Letters, 17(7), 1340–1343. https://doi.org/10.1109/LCOMM.2013.052013.122902.
Nam, P. M., Do, D.-T., Tung, N. T., & Tin, P. T. (2018). Energy harvesting assisted cognitive radio: random location-based transceivers scheme and performance analysis. Telecommunication Systems, 65(1), 123–132. https://doi.org/10.1007/s11235-017-0325-0.
Nguyen, T. T., Pham, N. M., & Do, D. T. (Dec. 2017). Wireless powered underlay cognitive radio network with multiple primary transceivers: Energy constraint, node arrangement, and performance analysis. International Journal of Communication Systems, 30(18), , https://doi.org/10.1002/dac.3372.
Nam, P. M., Duy, T. T., & Ca, P. V. (2019). Performance of cluster-based cognitive multihop networks under joint impact of hardware noises and non-identical primary co-channel interference. TELKOMNIKA Telecommunication, Computing, Electronics and Control, 17(1). https://doi.org/10.12928/telkomnika.v17i1.9543.
Gradshteyn, I. S., & Ryzhik, I. M. (2007). Table of integrals, series, and products (7th ed.). San Diego, CA: Elsevier Inc.
Yates, D. R., & Goodman, D. J. (1998). Probability and stochastic processes. Hoboken, NJ: Willey.
Rohatgi, V. K. (1976). An introduction to probability theory and mathematical statistics. New York: Wiley.
Papoulis, A. (1991). Probability, random variables, and stochastic processes (3rd ed.). New York: McGaw-Hill Inc.
Acknowledgements
This research is funded by Vietnam National Foundation for Science and Technology Development (NAFOSTED) under grant number 102.04-2017.317.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendices
1.1 Appendix A
Proof of Proposition 1 in (15)
From (3), denote \({\vartheta _i}\left( \upsilon \right) {=}\Pr \! \left( \!{\frac{{{M_i}}}{{\sum \nolimits _{j {=} 1,j \ne i}^{L^{\phantom {\frac{.}{.}}}} {\left( {{M_j}} \right) }{+}{M_{L {+} 1}} {+} 1}} {\le } \upsilon }\!\right) ,\) where \({M_i} \buildrel \varDelta \over ={\varOmega _i}{\kappa _{i,i}}\), \({M_j} \buildrel \varDelta \over ={\varOmega _i}{\kappa _{j,i}}\), \({M_{L + 1}} \buildrel \varDelta \over ={\varDelta _{k - 1}}{\varpi _{k - 1,i}}\), \(M \buildrel \varDelta \over =\sum \nolimits _{j = 1,j \ne i}^L{{M_j}}+{M_{L + 1}} = \sum \nolimits _{a = 1,a \ne i}^{L + 1}{{M_a}}.\) Using the law of total probability in [37, Lemma 1], the \({f_{M,i}}\left( x \right) \) is given by
where \({\beta _{{M_i}}} = {\delta _{i,i}}\), \({\beta _{{M_{L +1}}}} = {\varpi _{k - 1,i}}\), \({\beta _{{M_a}}} ={\delta _{a,i}}\). With the assistance of [41, 4.20], we easily find \({f_{M + 1,i}}\left( x \right) \). Next, the \({F_{M +1,i}} \left( x \right) \) can be derived by integration the \({f_{M+1,i}} \left( x \right) \).
After some algebra and changing variables, we have
Applying the complementary probability theory, \(1-{\vartheta _i}\left( \upsilon \right) \) is the success probability on ith pair. Therefore, \(1-\prod \nolimits _{i = 1}^L \left( {1-{\vartheta _i}\left( \upsilon \right) } \right) \) is the primary outage, on (15).
1.2 Appendix B
Proof of Proposition 2 in (18)
Substituting (5), (6), (7), the (13) is equivalent to
where \(\xi = {2^{K{C_{th}}}}\). We can rewrite (B.1) as
where \(X = {\varDelta _{k - 1}}{\varphi _k}\), \(\hat{X} = {\varDelta _{k - 1}}{\chi _k}\) have the mean \({\varepsilon _k},{\eta _k}\). \(Y = \sum \nolimits _{i = 1}^L {{Y_i}} ,\hat{Y} = \sum \nolimits _{i = 1}^L {{{\hat{Y}}_i}}\), with \({Y_i} = {\varOmega _i}{\omega _{i,k}}\), \({\hat{Y}_i} = {\varOmega _i}{\theta _i}\), are \({\tau _{i,k}},{\sigma _i}\), respectively. We derive the representative \(\Pr \left( {U = 1+X/\left( {Y+1} \right) <u} \right) \) in details. Based on [37, 12], [41, 4.20], we obtain the \(\Pr \left( {U \le u} \right) \) expression as follows (B.3), (B.4)
Let’s denote \(T = \frac{{\hat{X}}}{{\hat{Y}+1}}\), \(V = T+1\). We identified \({f_T}\left( t \right) \) by exploiting [42, 21] and solved the integration by [40, 3.381.4]. Afterwards, we apply [41, 4.20] to exchange between T and V random variables. We obtain
We exploit \({F_{\xi ,k}}\left( \xi \right) \!= \!{F_{U/V}}\left( \xi \right) \!=\! \int \nolimits _1^\infty {{f_V}\left( v \right) .} {F_U} \left( {v\xi } \right) dv,\) derived from [43, 6.42, 6.43]. The result shows in (B.6). Next, we can find the results of the \({Q_i},\;(i = 1,2,3,4)\), in (B.7) by [40, 3.351.4, 3.353.1, 3.352.2]. Substituting (B.7) to (B.6), we obtain (19), and substituting (19) to (18), we have \({\mathrm{SO}}{{\mathrm{P}}_{{\mathrm{e2}}e}}\).
1.3 Appendix C
Proof of Proposition 3 in (22)
Next, from (3), we consider the \({\mathrm{O}}{{\mathrm{P}}_k} =\Pr \left( {\frac{I}{{H+1}} < {\gamma _{th}}} \right) \), where \(I={\varDelta _{k - 1}}{\varphi _k},H = {H_1}+{H_2}...+{H_L} =\sum \nolimits _{i = 1}^L {{\varOmega _i}{\omega _{i,k}}}\),
Using the same methodology with the first proposition, we receive the \({\mathrm{O}}{{\mathrm{P}}_k}\) as follows
Afterwards, the \({\mathrm{O}}{{\mathrm{P}}_{e2e}}\) in (24) is derived following the substitution of \({\mathrm{O}}{{\mathrm{P}}_k}\) with (C.2) in (23).
1.4 Appendix D
From (4), let us denote
where \(P = {\varDelta _{k - 1}}{\chi _k},\;Q = {Q_1}+{Q_2}+\cdots +{Q_L} =\sum \nolimits _{i = 1}^L {{\varOmega _i}{\theta _i}}\). Likewise, the \({f_Q}\left( y \right) \) can be written as
Applying similar way above, we obtain the expression in (26).
Rights and permissions
About this article
Cite this article
Pham, M.N. On the secrecy outage probability and performance trade-off of the multi-hop cognitive relay networks. Telecommun Syst 73, 349–358 (2020). https://doi.org/10.1007/s11235-019-00608-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-019-00608-1