Abstract
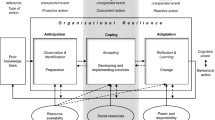
The protection of organizational information and information systems (IS) is a socio-technical issue and requires insiders take on a more proactive set of security roles. Accordingly, we contend that insiders’ abilities to enact these diverse information security roles can be explained by behavioral complexity theory. Adapted to the security context, behavioral complexity theory stipulates that insider’s ability to take appropriate precautions against organizational security threats is explained by their (1) repertoire of security roles and associated behaviors (i.e., security behavioral repertoire) and their (2) ability to switch from role to role (i.e., security behavioral differentiation). However, beyond behavioral complexity, protecting against complex security-related threats in the workplace requires significant psychological resources of insiders. Thus, to examine the influence of behavioral complexity on insiders’ protection motivation, we develop and examine an extended model of behavioral complexity including insiders’ workplace resilience—a significant work-related psychological resource Our results fully support the extended security behavioral complexity model’s role in driving an insider’s protection motivation.




Similar content being viewed by others
References
Anderson, C. L., & Agarwal, R. (2010). Practicing safe computing: A multimedia empirical examination of home computer user security behavioral intentions. MIS Quarterly, 34(3), 613–643.
August, T., & Tunca, T. I. (2006). Network software security and user incentives. Management Science, 52(11), 1703–1720.
Aurigemma, S., & Mattson, T. (2017). Privilege or procedure: Evaluating the effect of employee status on intent to comply with socially interactive information security threats and controls. Computers & Security, 66218–66234.
Avey, J. B., Reichard, R. J., Luthans, F., & Mhatre, K. H. (2011). Meta analysis of the impact of positive psychological capital on employee attitudes, behaviors, and performance. Human Resource Development Quarterly, 22(2), 127–152.
Ayyagari, R., Grover, V., & Purvis, R. (2011). Technostress: Technological antecedents and implications. MIS Quarterly, 35(4), 831–858.
Bagozzi, R. P. (2011). Measurement and meaning in information systems and organizational research: Methodological and philosophical foundations. MIS Quarterly, 35(2), 261–292.
Bande, B., Fernández-Ferrín, P., Varela, J. A., & Jaramillo, F. (2015). Emotions and salesperson propensity to leave: The effects of emotional intelligence and resilience. Industrial Marketing Management, 44142–44153.
Bapna R, Goes P, Gupta A, Jin Y (2004) User heterogeneity and its impact on electronic auction market design: An empirical exploration. MIS Quarterly21-43.
Barrett, F. J. (1998). Coda—Creativity and improvisation in jazz and organizations: Implications for organizational learning. Organization Science, 9(5), 605–622.
Baskerville, R., Spagnoletti, P., & Kim, J. (2014). Incident-centered information security: Managing a strategic balance between prevention and response. Information & Management, 51(1), 138–151.
Bateman, T. S., & Organ, D. W. (1983). Job satisfaction and the good soldier: The relationship between affect and employee "citizenship". Academy of Management Journal, 26(4), 587–595.
Bollen, K. A. (2011). Evaluating effect, composite, and causal indicators in structural equation models. MIS Quarterly, 35(2), 359–372.
Boss S, Kirsch L (2007) The last line of defense: Motivating employees to follow corporate security guidelines. Proceedings of the 28th International Conference on Information Systems, Montreal) paper 103.
Boss, S. R., Kirsch, L. J., Angermeier, I., Shingler, R. A., & Boss, R. W. (2009). If someone is watching, I'll do what I'm asked: Mandatoriness, control, and information security. European Journal of Information Systems, 18(2), 151–164.
Bulgurcu, B., Cavusoglu, H., & Benbasat, I. (2010). Information security policy compliance: An empirical study of rationality-based beliefs and information security awareness. MIS Quarterly, 34(4), 523–548.
Burns, A. J., Posey, C., Courtney, J. F., Roberts, T. L., & Nanayakkara, P. (2017a). Organizational information security as a complex adaptive system: Insights from three agent-based models. Information Systems Frontiers, 19(3), 509–524.
Burns AJ, Posey C, Roberts TL, Lowry PB (2017b) Examining the relationship of organizational insiders' psychological capital with information security threat and coping appraisals. Computers in Human Behavior(68):190-209.
Burns, A. J., Roberts, T. L., Posey, C., Bennett, R. J., & Courtney, J. F. (2018). Intentions to comply versus intentions to protect: A VIE theory approach to understanding the influence of insiders’ awareness of organizational SETA efforts. Decision Sciences, 49(6), 1187–1228.
Burns AJ, Roberts TL, Posey C, Lowry PB (2019) The adaptive roles of positive and negative emotions in organizational insiders’ security-based precaution taking. Information systems Research forthcoming.
Cenfetelli, R. T., & Bassellier, G. (2009). Interpretation of formative measurement in information systems research. MIS Quarterly, 33(4), 689–707.
Chen, G., Gully, S. M., Whiteman, J.-A., & Kilcullen, R. N. (2000). Examination of relationships among trait-like individual differences, state-like individual differences, and learning performance. Journal of Applied Psychology, 85(6), 835–847.
Chin WW (2010) How to write up and report PLS analyses. VE Vinzi, WW Chin, J Henseler, H Wang, eds. Handbook of Partial Least Squares (springer, New York, New York) 655-690.
D'Arcy, J., & Devaraj, S. (2012). Employee misuse of information technology resources: Testing a contemporary deterrence model. Decision Sciences, 43(6), 1091–1124.
D'Arcy, J., & Herath, T. (2011). A review and analysis of deterrence theory in the IS security literature: Making sense of the disparate findings. European Journal of Information Systems, 20(6), 643–658.
D'Arcy, J., & Hovav, A. (2007). Deterring internal information systems misuse. Communications of the ACM, 50(10), 113–117.
D'Arcy, J., Hovav, A., & Galletta, D. (2009). User awareness of security countermeasures and its impact on information systems misuse: A deterrence approach. Information Systems Research, 20(1), 79–98.
Denison, D. R., Hooijberg, R., & Quinn, R. E. (1995). Paradox and performance: Toward a theory of behavioral complexity in managerial leadership. Organization Science, 6(5), 524–540.
Diamantopoulos, A. (2011). Incorporating formative measures into covariance-based structural equation models. MIS Quarterly, 35(2), 335–358.
Diamantopoulos, A., & Winklhofer, H. M. (2001). Index construction with formative indicators: An alternative to scale development. Journal of Marketing Research, 38(2), 269–277.
Dlamini, M., Eloff, J. H., & Eloff, M. M. (2009). Information security: The moving target. Computers & Security, 28(3), 189–198.
Drucker PF (2011) The New Realities, (Routledge: Taylor and Francis. Kindle Edition, New York, New York).
Eckhardt, A., Laumer, S., & Weitzel, T. (2009). Who influences whom? Analyzing workplace referents' social influence on IT adoption and non-adoption. Journal of Information Technology, 24(1), 11–24.
Esposito Vinzi, V., Chin, W. W., Henseler, J., & Wang, H. (Eds.). (2010). Handbook of partial least squares: Concepts, methods and applications. New York, NY: Springer.
Hair, J. F., Hult, G. T. M., Ringle, C. M., & Sarstedt, M. (2014). A primer on partial least squares structural equations modeling (PLS-SEM). Los Angeles, California: Sage.
Henseler, J., Dijkstra, T. K., Sarstedt, M., Ringle, C. M., Diamantopoulos, A., Straub, D. W., Ketchen, D. J., Hair, J. F., Hult, G. T. M., & Calantone, R. J. (2014). Common beliefs and reality about PLS: Comments on Rönkkö and Evermann (2013). Organizational Research Methods, 17(2), 182–209.
Herath, T., & Rao, H. R. (2009). Protection motivation and deterrence: A framework for security policy compliance in organisations. European Journal of Information Systems, 18(2), 106–125.
Hobfoll, S. E. (1989). Conservation of resources: A new attempt at conceptualizing stress. American Psychologist, 44(3), 513–524.
Hobfoll, S. E. (2002). Social and psychological resources and adaptation. Review of General Psychology, 6(4), 307–324.
Hooijberg, R. (1996). A multidirectional approach toward leadership: An extension of the concept of behavioral complexity. Human Relations, 49(7), 917–946.
Jarvis, C. B., MacKenzie, S. B., & Podsakoff, P. M. (2003). A critical review of construct indicators and measurement model misspecification in marketing and consumer research. Journal of Consumer Research, 30(2), 199–218.
Johnston, A. C., & Warkentin, M. (2010). Fear appeals and information security behaviors: An empirical study. MIS Quarterly, 34(3), 549–566.
Kays, K., Gathercoal, K., & Buhrow, W. (2012). Does survey format influence self-disclosure on sensitive question items? Computers in Human Behavior, 28(1), 251–256.
Kumar, R. L., Park, S., & Subramaniam, C. (2008). Understanding the value of countermeasure portfolios in information systems security. Journal of Management Information Systems, 25(2), 241–280.
Lawrence, K. A., Lenk, P., & Quinn, R. E. (2009). Behavioral complexity in leadership: The psychometric properties of a new instrument to measure behavioral repertoire. The Leadership Quarterly, 20(2), 87–102.
Lee, J., & Lee, Y. (2002). A holistic model of computer abuse within organizations. Information Management & Computer Security, 10(2), 57–63.
Lee, Y., & Kozar, K. A. (2005). Investigating factors affecting the adoption of anti-spyware systems. Communications of the ACM, 48(8), 72–77.
Lee, Y., & Larsen, K. R. (2009). Threat or coping appraisal: Determinants of SMB executives’ decision to adopt anti-malware software. European Journal of Information Systems, 18(2), 177–187.
Lowry, P. B., D’Arcy, J., Hammer, B., & Moody, G. D. (2016). “Cargo cult” science in traditional organization and information systems survey research: A case for using nontraditional methods of data collection, including mechanical Turk and online panels. The Journal of Strategic Information Systems, 25(3), 232–240.
Lowry, P. B., & Gaskin, J. (2014). Partial least squares (PLS) structural equation modeling (SEM) for building and testing behavioral causal theory: When to choose it and how to use it. IEEE Transactions on Professional Communication, 57(2), 123–146.
Lowry, P. B., Moody, G., Vance, A., Jensen, M., Jenkins, J., & Wells, T. (2012). Using an elaboration likelihood approach to better understand the persuasiveness of website privacy assurance cues for online consumers. Journal of the American Society for Information Science and Technology, 63(4), 755–776.
Lowry, P. B., & Moody, G. D. (2015). Proposing the control-reactance compliance model (CRCM) to explain opposing motivations to comply with organisational information security policies. Information Systems Journal, 25(5), 433–463.
Luthans, F. (2002). The need for and meaning of positive organizational behavior. Journal of Organizational Behavior, 23(6), 695–706.
Luthans, F., Avolio, B. J., Avey, J. B., & Norman, S. M. (2007a). Positive psychological capital: Measurement and relationship with performance and satisfaction. Personnel Psychology, 60(3), 541–572.
Luthans, F., Vogelgesang, G. R., & Lester, P. B. (2006). Developing the psychological capital of resiliency. Human Resource Development Review, 5(1), 25–44.
Luthans, F., & Youssef, C. M. (2007). Emerging positive organizational behavior. Journal of Management, 33(3), 321–349.
Luthans, F., Youssef, C. M., & Avolio, B. J. (2007b). Psychological capital: Developing the human competitive edge. New York, New York: Oxford University Press. Kindle Edtion.
MacKenzie, S. B., Podsakoff, P. M., & Jarvis, C. B. (2005). The problem of measurement model misspecification in behavioral and organizational research and some recommended solutions. Journal of Applied Psychology, 90(4), 710–730.
Maddux, J. E., & Rogers, R. W. (1983). Protection motivation and self-efficacy: A revised theory of fear appeals and attitude change. Journal of Experimental Social Psychology, 19(5), 469–479.
Masten, A. S. (2001). Ordinary magic: Resilience processes in development. American Psychologist, 56(3), 227–238.
Messerschmidt, C. M., & Hinz, O. (2013). Explaining the adoption of grid computing: An integrated institutional theory and organizational capability approach. The Journal of Strategic Information Systems, 22(2), 137–156.
Njenga, K., & Brown, I. (2012). Conceptualising improvisation in information systems security. European Journal of Information Systems, 21(6), 592–607.
Pahnila S, Siponen M, Mahmood A (2007) Employees' behavior towards IS security policy compliance. Proceedings of the 40th Annual Hawaii International Conference on System Sciences, Waikoloa, Hawaii) 156-166.
Perols, J., Zimmermann, C., & Kortmann, S. (2013). On the relationship between supplier integration and time-to-market. Journal of Operations Management, 31(3), 153–167.
Petter, S., Straub, D. W., & Rai, A. (2007). Specifying formative constructs in information systems research. MIS Quarterly, 31(4), 623–656.
Podsakoff, P. M., MacKenzie, S. B., Lee, J. Y., & Podsakoff, N. P. (2003). Common method biases in behavioral research: A critical review of the literature and recommended remedies. Journal of Applied Psychology, 88(5), 879–903.
Posey, C., Roberts, T. L., & Lowry, P. B. (2015). The impact of organizational commitment on insiders’ motivation to protect organizational information assets. Journal of Management Information Systems, 32(4), 179–214.
Posey, C., Roberts, T. L., Lowry, P. B., Bennett, R. J., & Courtney, J. F. (2013). Insiders’ protection of organizational information assets: Development of a systematics-based taxonomy and theory of diversity for protection-motivated behaviors. MIS Quarterly, 37(4), 1189–1210.
Ringle CM, Wende S, Will A (2005) SmartPLS, release 2.0 (beta). SmartPLS, Hamburg, Germany URL http://www.smartpls.de.
Rönkkö M, Ylitalo J (2011) PLS marker variable approach to diagnosing and controlling for method variance. International Conference on Information Systems (AIS, Shanghai, China) paper 8.
Seligman, M., & Csikszentmihalyi, M. (2000). Positive psychology: An introduction. American Psychologist, 55(1), 5–14.
Siponen, M., Mahmood, M. A., & Pahnila, S. (2014). Employees’ adherence to information security policies: An exploratory field study. Information & Management, 51(2), 217–224.
Siponen M, Pahnila S, Mahmood A (2006) Factors influencing protection motivation and IS security policy compliance. Innovations in Information Technology (IEEE, Dubai) 1-5.
Siponen, M., & Vance, A. (2010). Neutralization: New insights into the problem of employee information systems security policy violations. MIS Quarterly, 34(3), 487–502.
Smith, W. K., & Lewis, M. W. (2011). Toward a theory of paradox: A dynamic equilibrium model of organizing. Academy of Management Review, 36(2), 381–403.
Stanton, J. M., Stam, K. R., Mastrangelo, P., & Jolton, J. (2005). Analysis of end user security behaviors. Computers & Security, 24(2), 124–133.
Straub, D. W. (1989). Validating instruments in MIS research. MIS Quarterly, 13(2), 147–169.
Straub, D. W., & Nance, W. (1990). Discovering and disciplining computer abuse in organizations: A field study. MIS Quarterly, 14(1), 45–60.
Sutcliffe KM, Vogus TJ (2003) Organizing for resilience. K Cameron, JE Dutton, RE Quinn, eds. Positive Organizational Scholarship (Berrett-Koehler, San Francisco, CA) 94-110.
Tugade, M. M., Fredrickson, B. L., & Feldman Barrett, L. (2004). Psychological resilience and positive emotional granularity: Examining the benefits of positive emotions on coping and health. Journal of Personality, 72(6), 1161–1190.
Vroom, C., & von Solms, R. (2004). Towards information security behavioural compliance. Computers & Security, 23(3), 191–198.
Wagnild, G. (2009). A review of the resilience scale. Journal of Nursing Measurement, 17(2), 105–113.
Wanberg, C. R., & Banas, J. T. (2000). Predictors and outcomes of openness to changes in a reorganizing workplace. Journal of Applied Psychology, 85(1), 132–142.
Williams, L. J., & Anderson, S. E. (1991). Job satisfaction and organizational commitment as predictors of organizational citizenship and in-role behaviors. Journal of Management, 17(3), 601–617.
Woon IMY, Low RT, Tan GW (2005) A protection motivation theory approach to home wireless security. Proceedings of the 26th International Conference on Information Systems, Las Vegas, NV, USA) paper 31.
Workman, M., Bommer, W. H., & Straub, D. W. (2008). Security lapses and the omission of information security measures: A threat control model and empirical test. Computers in Human Behavior, 24(6), 2799–2816.
Wu, Z., Steward, M. D., & Hartley, J. L. (2010). Wearing many hats: Supply managers' behavioral complexity and its impact on supplier relationships. Journal of Business Research, 63(8), 817–823.
Zafar, H., & Clark, J. G. (2009). Current state of information security research in IS. Communications of the Association for Information Systems, 24(1), 557–596.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix 1
Appendix 2
Rights and permissions
About this article
Cite this article
Burns, A.J., Posey, C. & Roberts, T.L. Insiders’ Adaptations to Security-Based Demands in the Workplace: An Examination of Security Behavioral Complexity. Inf Syst Front 23, 343–360 (2021). https://doi.org/10.1007/s10796-019-09951-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10796-019-09951-9